Compliance
Compliance refers to the responsibility and effort within a utility to adhere to laws, regulations, and standards that may be imposed on a national or regional level. Compliance may require deploying technical controls (such as firewalls), administrative controls (such as staff training), or physical controls (such as locks and fencing).
Importance
Directives from government and regulatory authorities define certain cybersecurity behaviors. Often, these behaviors are enforced through audits or inspections by the regulatory agency or through self-documentation on the part of the utility. While audits may seem burdensome, they are also an opportunity to get feedback from an outside party—the auditor—regarding security controls and accountability mechanisms. This feedback can serve as a fresh perspective that helps the utility achieve a stronger security posture.
Lack of compliance may be penalized. The regulatory agency may impose a fine, and depending on how these fines are determined and the severity of the violation, the financial impact may be severe (Workentin 2019). But the impact may be more than financial—lack of compliance can also impact reputation and customer trust (West 2019).
Regulations can motivate utility decision makers to make resources available for cybersecurity that might not otherwise be forthcoming. Some information technology managers have observed that without regulations, they might not get any funding from their bosses for cybersecurity. If laws and regulations are well structured, they can kick-start a utility’s cybersecurity program, which can then mature over time. (See the laws, regulations, and standards building block for a discussion of “well structured” versus “poorly structured” regulations.)
Intersections With Other Building Blocks
The compliance building block within the utility must identify all applicable laws, regulations, and standards and interpret how the recommended or required behaviors apply to the utility. The compliance building block then supplies high-level information regarding regulatory requirements to the governance building block. This enables utility leaders to make informed decisions regarding allocation of security resources. More detailed regulatory requirements are provided to the organizational security policy building block, so that the (externally driven) compliance efforts and the utility’s (internally driven) risk management efforts can be harmonized across the organization.
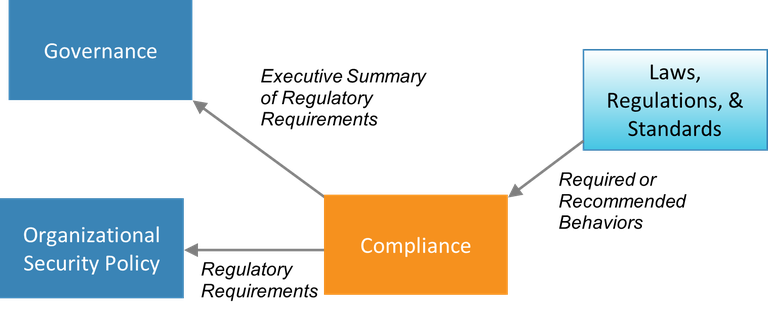
Figure 6. Information passed to and from the compliance building block
Process and Actions
Forming organizational policies that adhere to the cybersecurity behaviors and standards defined in regulations requires careful consideration. A solid first step is to identify someone who has experience with (or at least interest in) regulations and compliance, and who can take on the responsibility of leading the utility’s compliance effort. This person becomes the compliance officer for the utility.
The compliance officer leads groups of other employees (and possibly outside consultants) through the following processes:
- Research laws, regulations, and standards that apply to the utility and relate to cybersecurity, privacy, disclosure of cyber incidents, and related topics
- If regulations are structured with different levels of compliance—for instance, if larger generation facilities have a heavier regulator burden—determine which level of compliance applies to the utility and what compliance tasks need to be performed.
- Research any resources that assist in developing policies and procedures to help with compliance
- Interface with authorities and translate requirements within the organization
- Develop a process of gathering information about the compliance procedures and document incidents that are and are not in accordance with the enforced rules
- Develop compliance audit and review mechanisms internal to the organization
- Develop a reporting mechanism to submit periodic summaries of the compliance status.
Essential Data
When undertaking compliance, a utility should collect the following information:
- Government executive orders
- Standards and directives mandated by regulatory authorities
- Standards that the utility has elected to apply
- Regional/national/local laws and requirements
- A list of critical systems within the utility and the devices and applications running within those systems. The compliance officer will need this list if regulations specify specific controls for specific types of systems.






