Risk Management
Risk management is the practice of organizing and prioritizing risk throughout an organization. The needs and mission of the organization will determine the priority in which the risks are addressed. Risk cannot be eliminated entirely; there will always be some level of residual risk, even after mitigation. Determining how much risk the organization is willing to assume is a challenge every organization faces.
Importance
Managing cybersecurity risk is critical to the operation of an energy system and everything that relies on it. The risks an organization faces determine key areas that need special attention to avoid potential threats. Being aware of the risks will help an organization determine how much risk they are willing to assume. Once risks have been identified and prioritized, a plan of action can address and help mitigate vulnerabilities. (For a definition of “risk” and other risk management terms, see Box 2)
Risk management is a time- and labor-intensive process. Having a cybersecurity risk management strategy focused on avoidance, assessing, and mitigating risk will help provide structure and continuity to the organization.
Intersections With Other Building Blocks
Decisions about risk objectives are business decisions and thus are made at the highest level of the utility (by the board of directors, CEO, executive director, and so on). Is the objective of the utility to increase service reliability? Decrease incidents involving malware? Reduce cost? These decisions are part of the governance building block and are shared with the risk management building block in the form of risk objectives and business requirements.
Cybersecurity risk management touches every aspect of an organization and is dependent on good policies and procedures. The organizational security policy captures the utility’s approach to cyber risk management. This includes clearly identified roles and responsibilities, which create accountability for risks across the organization.
Risk management must take into account the changing threat landscape as expressed by CTI. Most utilities depend on outside sources for this information, which includes details of emerging threats (e.g., new hacking groups), new vulnerabilities (e.g., a newly discovered operating system security flaw), and new cyberattack tools (e.g., new malware).
Incorporating CTI into risk management enables a utility to identify possible threats and vulnerabilities and create a plan to mitigate them. This plan should include prioritizing the threats based on the level of risk identified by the organization. The higher the risk to mission-critical operations, the higher that threat should appear on the prioritized list.
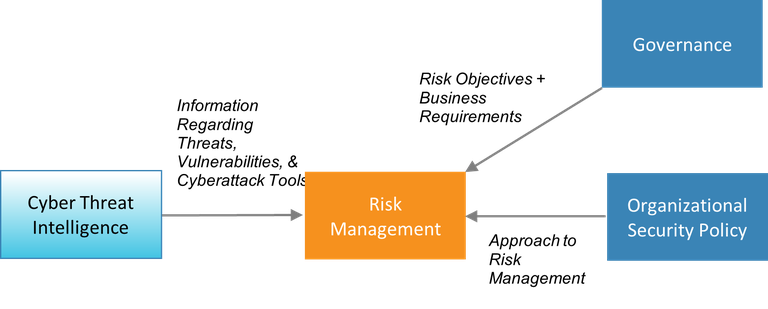
Figure 3. Information passed to and from the risk management building block
Process and Actions
Organizations have four choices when deciding how to handle risk:
- Avoid the risk. If an application or staff behavior introduces a risk, simply disallow it. For example, if employees checking their personal email on work computers is allowing malware onto the network, then do not allow personal email on work computers.
- Accept the risk. Access whether the risk is one that can be “lived with.” In making this decision, organizations need to carefully consider the potential harm that the risk represents and the likelihood of that risk coming to pass.
- Mitigate the risk. Put in place security controls that lower the amount of risk. For example, placing a firewall between an internal network and the public internet lowers the risk of a network-based attack. Note that it does not eliminate the risk completely; the intention is to bring the risk down to a level where it can be accepted. The risk remaining after a security control is added is referred to as residual risk.
- Transfer the risk. Make another party responsible for the risk. The classic example of this is purchasing insurance, which transfers the risk to an insurance company.
Decisions about how to handle different types of risk and other risk-related choices are best addressed through a risk management strategy. This will identify proper placement cybersecurity controls throughout the information technology (IT) and industrial control system (ICS) environments. The strategy should include regular vulnerability and risk assessments that will help determine which risks are present; these risks are then captured in a document called the risk register. Part of the risk management strategy is to select risk metrics to rank or prioritize risks. Creating the risk management strategy requires effort, but the payoff is streamlined business processes and decision making.
There are several different models and methodologies to aide in the risk management process. The items below are adapted and abridged from the Electricity Subsector Cybersecurity Risk Management Process.
A well-documented cybersecurity risk management strategy should include, but is not limited to, the following:
- Identify key stakeholders with their respective roles and responsibilities. The U.S. Department of Energy’s Risk Management Process lists many possible stakeholders including senior leaders, business process owners, chief information or security officers, and information system owners. However, not all of these are likely to have the availability and/or interest to participate in risk management activities.
- Define techniques and methodologies for assessing and prioritizing cybersecurity risks and vulnerabilities.
- Identify and prioritize the organization’s risks based on the mission and what is most critical, the likelihood the risk will be realized, and the severity of the impact if the risk is realized. This requires an understanding of systems and assets, their interconnections, communication parameters, and behaviors.
- Establish the organization’s risk tolerance. How much risk is the organization willing/able to assume? The organization’s risk tolerance should consider what it will take for the organization to recover should an event occur.
- Create a risk-aware business processes that account for cybersecurity threats and risks and recommend preventive actions.
- Identify and prioritize IT and ICS assets necessary to support the risk-aware business processes.
- Establish a process to routinely reassess a system’s cybersecurity posture based on new threat information, vulnerabilities, or system changes.
For a more detailed approach and description of the Risk Management Process, refer to the Electricity Subsector Cybersecurity Risk Management Process.
Essential Data
The utility should collect the following information as the cybersecurity risk management strategy is developed:
- A list of key organizational stakeholders
- Organization-wide risk management strategy: In other words, any existing strategies for risk management that are not specific to cybersecurity. The cybersecurity risk management strategy will need to be harmonized with these other strategies.
- Organization’s mission
- Organization’s strategic goals and objectives
- Current business processes for IT and ICS assets
- Asset inventory prioritized according to mission criticality
- Defined roles and responsibilities pertaining to cybersecurity.
Recommended Reading
Resilient Energy Platform. “Calculate Risks.” Accessed January 5, 2021.






