Power Sector Cybersecurity Building Blocks
Developed through the U.S. Agency for International Development (USAID)-National Renewable Energy Laboratory (NREL) Partnership and the Resilient Energy Platform, the Power Sector Cybersecurity Building Blocks are designed to help a variety of stakeholders improve security for the electrical grid.
This effort is focused on combatting and addressing cybersecurity challenges faced by small and under-resourced utilities and was grown out of USAID and NREL’s discussions with utilities around the world, along with past cybersecurity assessments performed by NREL on dozens of utilities and government agencies.
The Need
There are already many excellent guides, standards, and frameworks for organizations seeking to improve cybersecurity. However, despite the growing resources available, many organizations still struggle to create a cybersecurity program that is balanced across all required areas to protect their assets from attack.
Organizations may find themselves with too much investment in one area and little investment in another. By addressing each building block of cybersecurity, a balanced cybersecurity program is more attainable.
About the Building Blocks
The building blocks function as a guide to help organizations develop a robust cybersecurity defense program. Individually, each building block represents a cluster of related activities within cybersecurity on which an organization should focus. By using the building blocks, organizations can effectively prioritize their cybersecurity efforts to best thwart a wide range of potential cyberattacks.
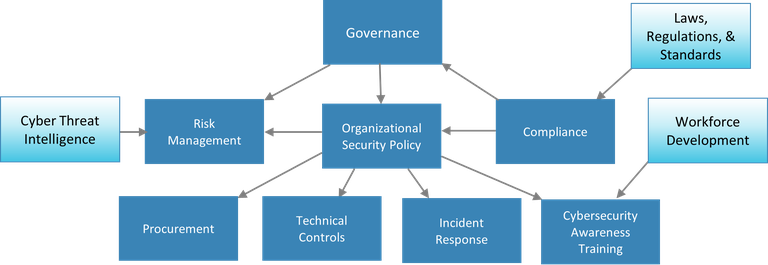
The 11 Cybersecurity Building Blocks include the following and each discuss a particular element of a well-rounded cybersecurity framework:
- Governance
- Organizational Security Policy
- Risk Management
- Cyber Threat Intelligence
- Laws, Regulations, and Standards
- Compliance
- Procurement
- Technical Controls
- Incident Response
- Cybersecurity Awareness Training
- Workforce Development
The Benefit
Organizations in the early stages of cybersecurity maturity will likely get the most benefit from these building blocks because they may struggle with the question of what a complete cyber program looks like. More mature cyber organizations can also use the building blocks to gain a fresh perspective on their efforts and fill in gaps in their existing cyber programs.
The Power Sector Cybersecurity Building Blocks are not meant to be the final word on cybersecurity for the power sector, as this field is evolving rapidly with the introduction of new power grid technology and an ever-changing threat landscape. USAID and NREL welcome discussion regarding updates to future iterations of these building blocks. For more information, please read the full report or view the fact sheet.
Learn More
Ask an Expert
The Resilient Energy Platform connects power system stakeholders across the globe to a network of cybersecurity resilience experts, providing remote consultation and advice at no cost.
Learn more and message the team.
Free Trainings
Ongoing Cybersecurity Building Blocks Webinar Series
USAID and NREL are partnering with CARILEC to offer a series of webinars based upon the Power Sector Cybersecurity Building Blocks. Each webinar offers a deep dive into the many issues utilities face when building a balanced cybersecurity plan to thwart attacks, minimize impacts, and get back to business quickly following an incident.
Register for the next training or watch the previous recordings below:
____________________________________________________________________________________________________
Webinar Recording: Governance: A Building Block for Power Sector Cybersecurity>>
Webinar Recording. Cybersecurity Awareness Training: A Building Block for Power Sector Cybersecurity
Webinar Recording: Cybersecurity Incident Response
Webinar Recording: Building Blocks to Support Cybersecurity in the Power Sector
Webinar Recording: Cybersecurity and Distributed Energy Resources






